Which of the Following Can Prevent Macros Attacks
Aideen sent an email to her supervisor explaining the Domain Name System Security Extensions DNSSEC. Select all that apply.

Infographic How To Prevent Malware Malware Security Solutions Infographic
It is fully supported in BIND9.

. Which of the following can the attacker match the hash to as a means to obtain the password. It adds additional resource records. C Macros can use absolute or relative cell referencing.
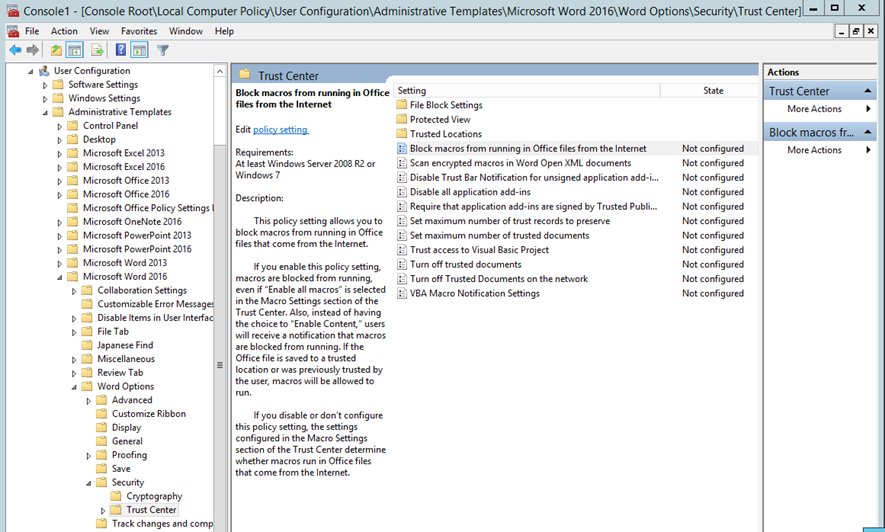
Leave Macros Alone. You can read more about this Group Policy setting at Plan security settings for VBA macros in Office 2016. You can disable macros on Microsoft programs by following these steps.
Creating a user account with Administrator privileges. VBA is a hardware network security device. Eavesdropping can be prevented by turning off NFC while in public while MITM attack can be protected by using strong passwords and PINs.
Documents whose macro processes look suspicious. Open the Block macros from running in Office files from the Internet setting to configure and enable it. User access is closely monitored and very restricted with no exceptions.
An attacker can exploit a weakness in a password protocol to calculate the hash of a password. Which of the following should be recommended as the FIRST line of defense to prevent this attack vector from reoccurring. Which of the following best describes mandatory physical control.
D Templates cannot contain macros. Go to the Word or Excel Menu. For more tips on protecting yourself from suspicious emails see.
Which of the following statements would Aideen have NOT included in her email. Malicious email attachments are designed to launch an attack on a users computer. Creating two user accounts.
Managing Macro Malware Attacks The best way eliminate the threat of macro malware is to reduce the amount of interaction between malware and a device. Select all that apply. Once the macros were enabled the antivirus software triggered an alert.
It is a reward program that is used to report individuals who hack against a company. Which of the following can prevent macros attacks. Which of the following is an attack where the attacker will often use a fake caller-ID to appear as a trusted organization and attempt to get the individual to enter account details via the phone.
Wi-Fi Protected Access WPA. Enterprises can prevent macro malware from running executable content using ASR rules. Some of these infections can allow the.
Click Administrative templates Microsoft Word 2016 Word options Security Trust Center. A company recently experienced a security incident in which an unauthorized user was able to insert a USB flash drive into a kiosk launch a non-native OS and deliver malicious payloads across the network. Static secure MAC addresses A switch port may be manually configured with the specific MAC address of the device that connects to it.
A Macros are created using VBA. Common needs are predetermined and access is allowed with the same key. A virus requires user interaction to infect a.
VBA Protected view Private DNS server PowerShell 13. Which of the following differentiates a virus from a worm. Which of the following is not true about macros.
VBA is a command language interpreter. Attackers attach these files to email that can install malware capable of destroying data and stealing information. The malicious activity was stepped by the antivirus software.
How is the malicious actor. The attachments within these malicious emails can be disguised as documents PDFs e-files and voicemails. One with high privileges and one with lower privileges.
What type of attacks can this type of security prevent. Each individual has a unique key that corresponds to his or her access. Spam emails are the main way macro malware spreads.
If you dont need to use them you should definitely have them turned off Van Pelt says. Eavesdropping can be prevented by being aware of ones surroundings while using NFC technology while MITM attack can be prevented by configuring in a pairing method so only one side can send and the other can receive it at a time. A ____ attack is when the hackers motivation is to prevent legitimate access to a companys website not to steal or destroy information.
One of the several ways you can prevent CAM table overflow attacks is to configure your switch port security on the switch. It is not necessary to buy a software specifically for the purpose of blocking macro malware attackers. Pre-Shared Key PSK B.
The script includes a few macros designed to secretly gather and send information to a remote server. Select Disable All Macros Without Notification Macro viruses are now more sophisticated than when they first came out in the nineties. Which of the following can the attacker match the hash to as a means to obtain the password.
You can apply port security in three ways. Privilege escalation is a hacking method to increase privileges on a user account. Select all that apply A.
Access is delegated to parties responsible for that building or room. The Worlds Largest Repository of Historical DNS data. It can prevent a DNS transfer attack.
How To Stop Prevent CAM Table Overflow Attacks. VBA is an event-driven programming language. Delete any emails from unknown people or with suspicious content.
VBA is a network assessment tool. Which of the following security measures would have been BEST to prevent the attack from being executed in the first place Select TWO. A MITM attack occurs between two endpoints whereas a MITB attack occurs between a browser and web server.
Which of the following correctly differentiates between a man-in-the-middle MITM attack and a man-in-the-browser MITB. Choose Preferences from the dropdown options. B Macros can be saved in XLSM workbooks.
A virus can only infect a single machine. It adds message header information. Thats the major way these viruses get in.
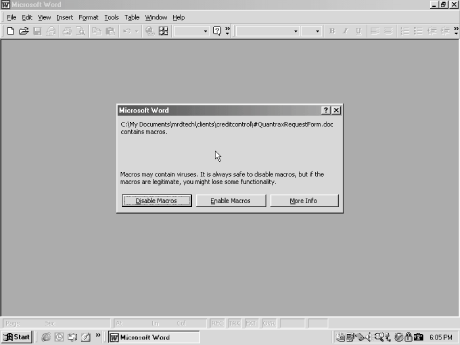
A worm can infect multiple machines. Heres what to do if you think a Word or Excel document contains a. A virus requires user interaction to infect a machine.
Its a good idea to use a reliable security software to help remove macro viruses. When Ann opened the attachment she was prompted to enable macros. The biggest tip to make sure you dont run into any security issues through macros is dont enable them.
A worm requires user interaction to infect a machine. Which specific type of attack occurs when a threat actor redirects network traffic by modifying the local host file to send legitimate traffic. Most trusted antivirus software prevents macros from downloading malware to your computer.
Increasing privileges on a user account.

Pin On Prodefence Security News

Guide To Prevent Execution Of Excel 4 0 Macro Malware Microsoft Office 365 Product Asec Blog
Intel Insight How To Disable Macros

What Is Macro Virus Types And Methods To Prevent Macro Virus

Microsoft Restricts Xlm Macros In Excel To Prevent Malware Attacks Simpleitpro

How To Protect Computers From Macro Virus

Restricting Or Blocking Office 2016 2019 Macros With Group Policy 4sysops

14 Likes 0 Comments Mirykle Thevegans0ul On Instagram T U R M E R I C H Turmeric Health Benefits Turmeric Benefits Coconut Health Benefits

Solved 12 Which Of The Following Can Prevent Macros Chegg Com

Ingredients For A Healthy Heart Heart Healthy Heart Healthy Diet Heart Health Month

What Are Macro Viruses And How Do They Work
Macro Malware And Secure Documents What You Need To Know Sap Blogs
/img_02.png?width=918&name=img_02.png)
Macro Virus What Is It How To Remove It Avg

How To Launch Malicious Macros Unnoticed On Macos Kaspersky Official Blog

6 Symptoms Of A Heart Attack That Occurs Only In Women Heart Attack Symptoms Good Health Tips Health Tips
What Is A Macro Virus Protection And Preventive Measures

Eye Iris Pupil 目 œil Glaz Occhio Ojo Color Texture Pattern Macro Macro Of Blue Female Eye Stock Photo 144817270 Eyes Healthy Eyes

Comments
Post a Comment